
Cyberthreats in the automotive industry are becoming more and more relevant, and incidents related to automotive cybersecurity are attracting the attention of experts all over the world. According to the Upstream report, the number of cyberattacks on automotive vehicles increased by 99% during the period from 2019 through 2020, and in 2022 the number of attacks on automotive APIs grew by 380%, which made up 12% of the total number of incidents. These figures were high despite the state-of-the-art cybersecurity measures that were implemented by the giants of the automotive industry. In 2023, more than 20 million hack attempts related to automotive systems were registered. One of the more glaring examples of these types of vulnerabilities was identified by researchers in the remote control system for KIA vehicles in June of 2024. Although there is no reliable, publicly available data on any previous hacker exploitation of this vulnerability or any related user data leaks, the company incurred significant damage to its reputation.

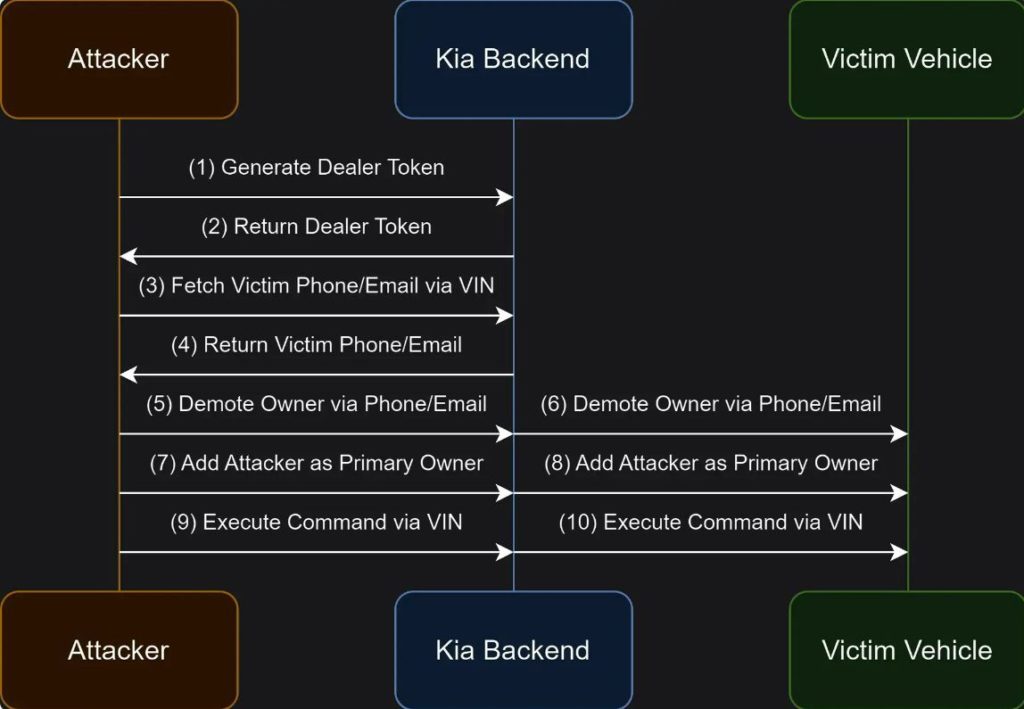
The main problem was that dealers had extensive access to KIA vehicle control systems, including access to vehicles they did not actually own. When creating a user account on the dealer portal, hackers were able to get a dealership token and then use it to send commands to cars and control them remotely.
Dealerships basically had access to all the functions of a vehicle without proper verification of who was actually requesting control of the vehicle. Today, we see that systems being used in the infrastructure of auto manufacturers and even further down the supply chain are not performing a sufficient number of required verifications. For example, just because an app does not have a button for a specific command does not mean that this command cannot be sent via a cloud service API.
Modern automotive vehicles like the ones produced by KIA use cloud services to manage various functions, such as opening doors and managing the security alarm or lighting. In the case of KIA, the dealer portal allowed any registered user to manage these functions if they knew the vehicle’s VIN number (obtained based on the license plate number) and had a dealership token.
We should clarify that the license plate number alone does not actually provide access to vehicle systems, but hackers were able to use a third-party service to convert a license plate number into a VIN. These types of services are provided by legitimate software. Although the VIN served as the key identifier for the API, it was still not enough for an attack.
To conduct an attack, the hacker had to obtain access to the KIA dealer portal. This was accomplished by creating a dealership account with arbitrary data. As it turned out, the car manufacturer’s website did not verify or authenticate the registration data that was used. After registration, the user received a token that let them send programming calls to the backend API of the dealership. This token was used in combination with the VIN to send commands to control the vehicle.
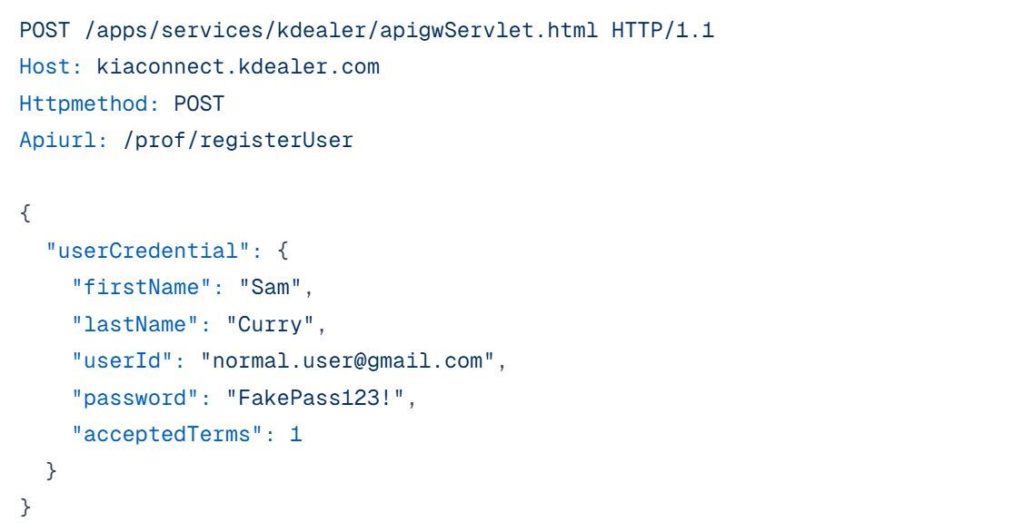
In other words, the minimum data required for a successful attack consisted of the following:
As you can see, the vulnerability was linked to insufficient verification of access rights by the dealership API, which allowed hackers to send commands to vehicles without verification of their ownership of the vehicle. This API allowed them to send commands to cloud services so that these commands were then executed by the vehicle. In other words, with a minimal set of data, you could have controlled any KIA vehicle that was manufactured in 2014 or later (according to official data, each year the KIA Corporation produces 0.5 million vehicles, which are sold all over the world). All those vehicles were vulnerable to an attack.
The main flaw was not a specific vulnerability in the code, but in the system architecture. When it comes to cybersecurity, companies are advised to follow the principle of least privilege (PoLP) to enhance their security. According to this principle, each user must only have the specific rights they need to perform their specific tasks, and no other rights. In the case we are discussing here, dealerships had access to all vehicles without any verifications or restrictions.
This design error enabled hackers to gain access to vehicles without any connection to the vehicle owners. The proper access rights restrictions were not in place. This is a fundamental error that should be considered when designing this type of system.
Firstly, this vulnerability simplifies car theft. Secondly, it facilitates the collection of personal data from car owners. For example, a vehicle’s geolocation can be used to track its owner, which is definitely a security threat. In this specific case with KIA, hackers were able to gain access to the car owners’ home addresses, phone numbers, and other personal and sensitive information.
It is also extremely important to protect the data and functions of the vehicle itself, especially when it comes to sensitive systems such as remote control. Car manufacturers need to be very clear about the level of rights they give to dealerships. When it comes to the security of these systems, it is crucial to ensure that no one has access to all vehicle functions without clear authorization.
1. Proper authentication and access control. It is important to correctly configure the authentication system to verify the rights of each user. A dealership must only have access to the specific data and functions it needs to work with a specific vehicle.
2. Enhanced security of dealer portals. Dealer registration portals must have multi-level authentication and strict controls. This helps prevent hackers from registering as official dealers. Proper integration of procedures such as Know Your Customer (KYC) could have prevented unauthorized access to the dealer portal.
3. Secure APIs. If a vehicle control system uses APIs to interact with the cloud, it is important to think carefully about the process of verifying requests and determining which functions are available based on those requests. This is a critical step in preventing hacking.
The security of these types of systems can be ensured by using technologies designed to protect these platforms. For example, the system known as Kaspersky Automotive Secure Gateway (KASG) was built for this purpose. Unlike the solutions used by KIA, we provide a secure-by-design (Cyber Immune) approach that helps isolate and restrict access to specific functions of a vehicle. We always verify who is requesting what, and this helps protect vehicles from unauthorized access.
Security solutions must be designed to not only prevent hacking, but also to eliminate design errors. We help car manufacturers and infrastructure providers incorporate security from the ground up by implementing security mechanisms that exclude the types of architectural errors that occurred at KIA.

After the vulnerability was detected and disclosed by researchers, KIA acknowledged a serious security issue with its dealer portal, confirming that the vulnerability allowed hackers to gain unauthorized access to vehicle owners’ information and control certain vehicle functions. Although the company took immediate steps to resolve the issue, the incident served as an important signal to automotive manufacturers who were once again forced to take a closer look at the security of cloud services and remote control of their vehicles.
In 2018, a vulnerability was detected in the mobile app Blue Link, which was used to remotely control Hyundai vehicles. This vulnerability allowed hackers to control vehicle doors and start the engine.
In 2021, cybersecurity researchers detected over 100 vulnerabilities in the software and hardware components of various brands of vehicles, including Tesla, Toyota, Volkswagen and others. These vulnerabilities affected various systems, including remote control systems, interfaces for mobile device communication, and even driver assistance systems.
In 2021, a cybersecurity researcher detected a vulnerability in Tesla’s autopilot system that could allow remote control of the vehicle. A hacker could have gained access to the system through a vulnerability in the web interface used for updates and diagnostics.
In 2021, a vulnerability was detected in the software of Ford electric vehicles that allowed attackers to remotely change the settings of batteries and charging systems. This vulnerability was linked to lost or poorly protected keys used for remote configuration.
Cyberattacks in the automotive industry can result in substantial economic losses, as demonstrated by an incident involving attacks on Volkswagen in 2021. In these attacks, hacked data on users and vehicle systems resulted in losses to the company of more than $50 million when it was discovered that the hackers were offering the hacked data for sale.
In 2022, nearly 7 GB of data from the Ferrari website was posted on the dark web. The hackers announced that they had gained access to internal documents, technical details, repair and maintenance documentation, and other information. This spring, researchers from a major Portuguese cybersecurity company detected a website vulnerability, or more specifically a vulnerability in one of the plug-ins of a content management system.
Back in 2022, Toyota reported a leak involving the personal data of 296,000 users of the T-Connect app. It turned out that an app development contractor inadvertently uploaded a portion of the source code to GitHub and this code included the access key to the company server. In early 2023, an independent researcher detected a number of vulnerabilities when entering the Toyota system using a backdoor mechanism for logging in to the website. The researcher gained full access to internal projects, documents and user accounts, including those of the company’s external partners and suppliers.
In 2023, a group of hackers declared that they had hacked Nissan’s corporate systems in Australia and New Zealand. The company confirmed that this hack resulted in leaked information about 100,000 people whose data was also put up for sale. In 2023, the Automotive Cybersecurity Report from S&P showed that 80% of new vehicles have the ability to connect to the internet, thereby increasing the number of potential attack vectors. Moreover, 95% of all vehicles manufactured in 2025 will have these capabilities, making these security issues even more pressing.

Cyberthreats in the automotive industry are becoming more and more relevant, and incidents related to automotive cybersecurity are attracting the attention of experts all over the world. According to the Upstream report, the number of cyberattacks on automotive vehicles increased by 99% during the period from 2019 through 2020, and in 2022 the number of attacks on automotive APIs grew by 380%, which made up 12% of the total number of incidents. These figures were high despite the state-of-the-art cybersecurity measures that were implemented by the giants of the automotive industry. In 2023, more than 20 million hack attempts related to automotive systems were registered. One of the more glaring examples of these types of vulnerabilities was identified by researchers in the remote control system for KIA vehicles in June of 2024. Although there is no reliable, publicly available data on any previous hacker exploitation of this vulnerability or any related user data leaks, the company incurred significant damage to its reputation.

The main problem was that dealers had extensive access to KIA vehicle control systems, including access to vehicles they did not actually own. When creating a user account on the dealer portal, hackers were able to get a dealership token and then use it to send commands to cars and control them remotely.
Dealerships basically had access to all the functions of a vehicle without proper verification of who was actually requesting control of the vehicle. Today, we see that systems being used in the infrastructure of auto manufacturers and even further down the supply chain are not performing a sufficient number of required verifications. For example, just because an app does not have a button for a specific command does not mean that this command cannot be sent via a cloud service API.
Modern automotive vehicles like the ones produced by KIA use cloud services to manage various functions, such as opening doors and managing the security alarm or lighting. In the case of KIA, the dealer portal allowed any registered user to manage these functions if they knew the vehicle’s VIN number (obtained based on the license plate number) and had a dealership token.
We should clarify that the license plate number alone does not actually provide access to vehicle systems, but hackers were able to use a third-party service to convert a license plate number into a VIN. These types of services are provided by legitimate software. Although the VIN served as the key identifier for the API, it was still not enough for an attack.
To conduct an attack, the hacker had to obtain access to the KIA dealer portal. This was accomplished by creating a dealership account with arbitrary data. As it turned out, the car manufacturer’s website did not verify or authenticate the registration data that was used. After registration, the user received a token that let them send programming calls to the backend API of the dealership. This token was used in combination with the VIN to send commands to control the vehicle.

In other words, the minimum data required for a successful attack consisted of the following:
As you can see, the vulnerability was linked to insufficient verification of access rights by the dealership API, which allowed hackers to send commands to vehicles without verification of their ownership of the vehicle. This API allowed them to send commands to cloud services so that these commands were then executed by the vehicle. In other words, with a minimal set of data, you could have controlled any KIA vehicle that was manufactured in 2014 or later (according to official data, each year the KIA Corporation produces 0.5 million vehicles, which are sold all over the world). All those vehicles were vulnerable to an attack.
The main flaw was not a specific vulnerability in the code, but in the system architecture. When it comes to cybersecurity, companies are advised to follow the principle of least privilege (PoLP) to enhance their security. According to this principle, each user must only have the specific rights they need to perform their specific tasks, and no other rights. In the case we are discussing here, dealerships had access to all vehicles without any verifications or restrictions.
This design error enabled hackers to gain access to vehicles without any connection to the vehicle owners. The proper access rights restrictions were not in place. This is a fundamental error that should be considered when designing this type of system.
Firstly, this vulnerability simplifies car theft. Secondly, it facilitates the collection of personal data from car owners. For example, a vehicle’s geolocation can be used to track its owner, which is definitely a security threat. In this specific case with KIA, hackers were able to gain access to the car owners’ home addresses, phone numbers, and other personal and sensitive information.
It is also extremely important to protect the data and functions of the vehicle itself, especially when it comes to sensitive systems such as remote control. Car manufacturers need to be very clear about the level of rights they give to dealerships. When it comes to the security of these systems, it is crucial to ensure that no one has access to all vehicle functions without clear authorization.

1. Proper authentication and access control. It is important to correctly configure the authentication system to verify the rights of each user. A dealership must only have access to the specific data and functions it needs to work with a specific vehicle.
2. Enhanced security of dealer portals. Dealer registration portals must have multi-level authentication and strict controls. This helps prevent hackers from registering as official dealers. Proper integration of procedures such as Know Your Customer (KYC) could have prevented unauthorized access to the dealer portal.
3. Secure APIs. If a vehicle control system uses APIs to interact with the cloud, it is important to think carefully about the process of verifying requests and determining which functions are available based on those requests. This is a critical step in preventing hacking.
The security of these types of systems can be ensured by using technologies designed to protect these platforms. For example, the system known as Kaspersky Automotive Secure Gateway (KASG) was built for this purpose. Unlike the solutions used by KIA, we provide a secure-by-design (Cyber Immune) approach that helps isolate and restrict access to specific functions of a vehicle. We always verify who is requesting what, and this helps protect vehicles from unauthorized access.
Security solutions must be designed to not only prevent hacking, but also to eliminate design errors. We help car manufacturers and infrastructure providers incorporate security from the ground up by implementing security mechanisms that exclude the types of architectural errors that occurred at KIA.

After the vulnerability was detected and disclosed by researchers, KIA acknowledged a serious security issue with its dealer portal, confirming that the vulnerability allowed hackers to gain unauthorized access to vehicle owners’ information and control certain vehicle functions. Although the company took immediate steps to resolve the issue, the incident served as an important signal to automotive manufacturers who were once again forced to take a closer look at the security of cloud services and remote control of their vehicles.
In 2018, a vulnerability was detected in the mobile app Blue Link, which was used to remotely control Hyundai vehicles. This vulnerability allowed hackers to control vehicle doors and start the engine.
In 2021, cybersecurity researchers detected over 100 vulnerabilities in the software and hardware components of various brands of vehicles, including Tesla, Toyota, Volkswagen and others. These vulnerabilities affected various systems, including remote control systems, interfaces for mobile device communication, and even driver assistance systems.
In 2021, a cybersecurity researcher detected a vulnerability in Tesla’s autopilot system that could allow remote control of the vehicle. A hacker could have gained access to the system through a vulnerability in the web interface used for updates and diagnostics.
In 2021, a vulnerability was detected in the software of Ford electric vehicles that allowed attackers to remotely change the settings of batteries and charging systems. This vulnerability was linked to lost or poorly protected keys used for remote configuration.
Cyberattacks in the automotive industry can result in substantial economic losses, as demonstrated by an incident involving attacks on Volkswagen in 2021. In these attacks, hacked data on users and vehicle systems resulted in losses to the company of more than $50 million when it was discovered that the hackers were offering the hacked data for sale.
In 2022, nearly 7 GB of data from the Ferrari website was posted on the dark web. The hackers announced that they had gained access to internal documents, technical details, repair and maintenance documentation, and other information. This spring, researchers from a major Portuguese cybersecurity company detected a website vulnerability, or more specifically a vulnerability in one of the plug-ins of a content management system.
Back in 2022, Toyota reported a leak involving the personal data of 296,000 users of the T-Connect app. It turned out that an app development contractor inadvertently uploaded a portion of the source code to GitHub and this code included the access key to the company server. In early 2023, an independent researcher detected a number of vulnerabilities when entering the Toyota system using a backdoor mechanism for logging in to the website. The researcher gained full access to internal projects, documents and user accounts, including those of the company’s external partners and suppliers.
In 2023, a group of hackers declared that they had hacked Nissan’s corporate systems in Australia and New Zealand. The company confirmed that this hack resulted in leaked information about 100,000 people whose data was also put up for sale. In 2023, the Automotive Cybersecurity Report from S&P showed that 80% of new vehicles have the ability to connect to the internet, thereby increasing the number of potential attack vectors. Moreover, 95% of all vehicles manufactured in 2025 will have these capabilities, making these security issues even more pressing.