
Modern cybersystems are characterized by the interpenetration of information (IT) and operational (OT) technologies: industrial, transportation, financial, scientific, etc. Cybersystems are becoming increasingly complex, and the amount of program code that determines their operation is growing. For example, according to McKinsey & Company 1, today’s cars contain 10 times more lines of code than in 2010, and there are more than 100 million lines of code in premium brand cars.
This increasing complexity of systems is exacerbated by their growing heterogeneity, global availability and high-speed transfer of large amounts of data. For example, while mobile networks previously focused on user-to-service or user-to-user content delivery, 5G networks bring high-speed cybersystem-to-cybersystem communications to the fore.
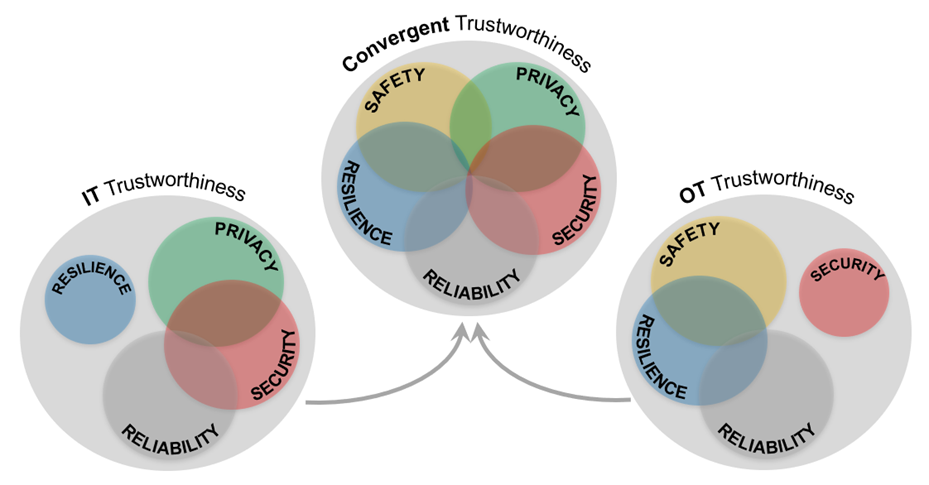
The convergence of OT and IT has changed the very notion of security. In the past, cybersystems were used to process data, and security was understood to be the integrity, confidentiality and availability aspects of that data. Today, functional security, resilience, operational reliability, and other aspects of system security determined by data processing are also becoming important2.
Cybersecurity problems directly impact the ability of systems to perform their critical functions, which has financial implications – cybersecurity risks related to the development, maintenance and support of systems are on the rise. According to a Kaspersky study3, 53% of organizations have abandoned new business projects because of the inability to address cybersecurity risks, and 74% have been confronted with the lack of a suitable security solution.
The rise in cybersecurity risks and compensation costs is due to several factors, including:
Developing and maintaining secure cybersystems presents a number of challenges, including:
When developing software or hardware products, the issue of security arises near the end of the project because security requirements are typically viewed as non-functional. In this case, security measures implemented in isolation from the core functionality of the product often leave loopholes for an attacker and do not provide effective defense against attacks.
The most common approach to solving these problems is the use of additional security measures. Industry best practices also include security audits and update management of OT and IT network components, cybersecurity awareness training for personnel, and continuous monitoring of the changing threat landscape. These solutions and practices remain popular and in demand for systems and technologies that are being actively operated, but there is another way to strengthen defenses – at the architectural level.
We will discuss the practical implementation of architecturally secure systems in a series of articles. In the second part, we describe an alternative approach to building secure information systems – the concept of Secure by Design.

Modern cybersystems are characterized by the interpenetration of information (IT) and operational (OT) technologies: industrial, transportation, financial, scientific, etc. Cybersystems are becoming increasingly complex, and the amount of program code that determines their operation is growing. For example, according to McKinsey & Company 1, today’s cars contain 10 times more lines of code than in 2010, and there are more than 100 million lines of code in premium brand cars.
This increasing complexity of systems is exacerbated by their growing heterogeneity, global availability and high-speed transfer of large amounts of data. For example, while mobile networks previously focused on user-to-service or user-to-user content delivery, 5G networks bring high-speed cybersystem-to-cybersystem communications to the fore.
The convergence of OT and IT has changed the very notion of security. In the past, cybersystems were used to process data, and security was understood to be the integrity, confidentiality and availability aspects of that data. Today, functional security, resilience, operational reliability, and other aspects of system security determined by data processing are also becoming important2.

Cybersecurity problems directly impact the ability of systems to perform their critical functions, which has financial implications – cybersecurity risks related to the development, maintenance and support of systems are on the rise. According to a Kaspersky study3, 53% of organizations have abandoned new business projects because of the inability to address cybersecurity risks, and 74% have been confronted with the lack of a suitable security solution.
The rise in cybersecurity risks and compensation costs is due to several factors, including:
Developing and maintaining secure cybersystems presents a number of challenges, including:
When developing software or hardware products, the issue of security arises near the end of the project because security requirements are typically viewed as non-functional. In this case, security measures implemented in isolation from the core functionality of the product often leave loopholes for an attacker and do not provide effective defense against attacks.
The most common approach to solving these problems is the use of additional security measures. Industry best practices also include security audits and update management of OT and IT network components, cybersecurity awareness training for personnel, and continuous monitoring of the changing threat landscape. These solutions and practices remain popular and in demand for systems and technologies that are being actively operated, but there is another way to strengthen defenses – at the architectural level.
We will discuss the practical implementation of architecturally secure systems in a series of articles. In the second part, we describe an alternative approach to building secure information systems – the concept of Secure by Design.