
When creating complex software products, it is almost impossible and quite wasteful to write all the code from scratch. The existing implementations of the USB stack or components for communication with network or file system comprise hundreds of thousands of code lines. Reinventing them would cost a lot and greatly increase the development time.
The use of open source software is a prevailing software development approach. According to the 2023 report by Synopsys, which analyzed over 1,700 applications, most of them (96%) contained open source. 76% of total application codebase was open source code.
There are no downsides to open source from the looks of it. You just take an appropriately licensed code, port it to your platform of choice, customize it to fit the task at hand, test it – and it’s done. However, open source software comes with its own risks. It may contain accidental/intentional vulnerabilities or malicious code.
The problem of trust in open source is especially critical for products with heightened security requirements. It takes extra code validation and analysis effort to address that problem. We at Kaspersky have started a service to track open source backdoors and vulnerabilities called Kaspersky Open Source Software Threats Data Feed. As of the end of 2022, it contained data on 3,000 vulnerable and malicious packets stored in popular repositories. Around 35% of exposed vulnerabilities are of high danger level, and another 10% are of critical danger level.
Third-party software in solutions based on KasperskyOS
The Cyber Immunity approach seems to be cut out to solve the problem of using code of unknown quality. And KasperskyOS is the ideal platform to implement this approach. This microkernel operating system enables the creation of inherently Cyber Immune solutions from a variety of small building blocks. This is possible thanks to the principles of isolation and control of interactions implemented in KasperskyOS. Of course, you have to follow a special methodology to develop a Cyber Immune solution: articulate security objectives and assumptions, use a proper approach to architecture design, employ the right SDL practices and various testing methods.
For details on the Cyber Immunization process, refer to the article “How we built a Cyber Immune product using an open source library: stages, pitfalls, solutions”. In that article, Sergey Yakovlev, the head of the KasperskyOS-based thin client development team, discusses at length how various open source components were used to create a real commercial product featuring Cyber Immunity, and how these had to me modified.
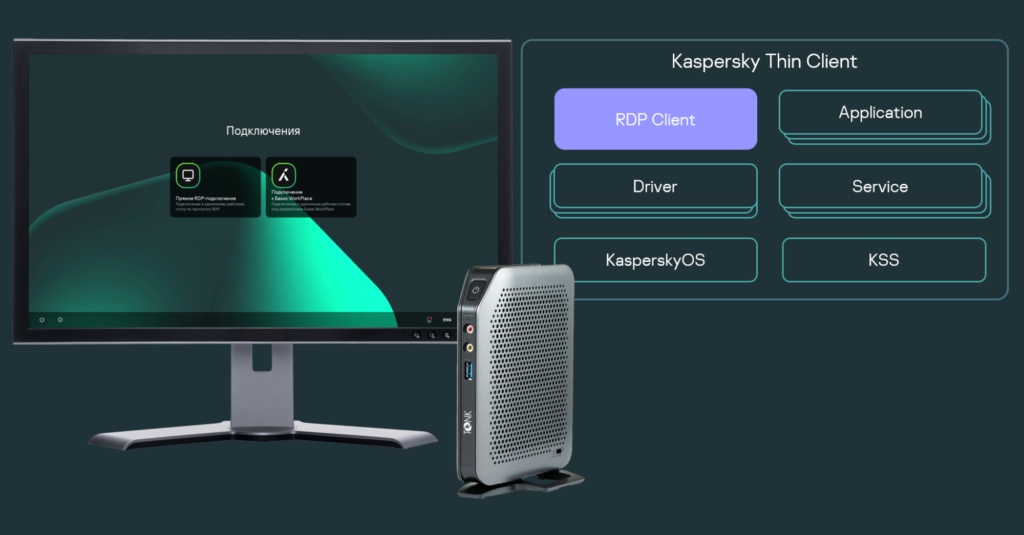
Third-party software in solutions based on KasperskyOS
The Cyber Immunity approach seems to be cut out to solve the problem of using code of unknown quality. And KasperskyOS is the ideal platform to implement this approach. This microkernel operating system enables the creation of inherently Cyber Immune solutions from a variety of small building blocks. This is possible thanks to the principles of isolation and control of interactions implemented in KasperskyOS. Of course, you have to follow a special methodology to develop a Cyber Immune solution: articulate security objectives and assumptions, use a proper approach to architecture design, employ the right SDL practices and various testing methods.
For details on the Cyber Immunization process, refer to the article “How we built a Cyber Immune product using an open source library: stages, pitfalls, solutions“. In that article, Sergey Yakovlev, the head of the KasperskyOS-based thin client development team, discusses at length how various open source components were used to create a real commercial product featuring Cyber Immunity, and how these had to me modified.
The cost of porting open source to KasperskyOS
This is fairly simple thanks to the almost full POSIX compatibility of KasperskyOS. The article will take you through the process of porting a FreeRDP library to a thin client’s operating system. This is an open source implementation of an RDP client – a component for connection to remote desktops via Remote Desktop protocol by Microsoft. Despite the library’s fair size – about 400,000 lines of code – not so many modifications were required. Some functions had to be added; unsupported ones were removed, such as fork(). Almost all functions were tested, some defects were spotted and corrected. It took about 30 commits, which you must agree, isn’t that much.
For all those interested in the details of Cyber Immune development, we recommend the article “How we built a Cyber Immune product using an open source library: stages, pitfalls, solutions“.

When creating complex software products, it is almost impossible and quite wasteful to write all the code from scratch. The existing implementations of the USB stack or components for communication with network or file system comprise hundreds of thousands of code lines. Reinventing them would cost a lot and greatly increase the development time.
The use of open source software is a prevailing software development approach. According to the 2023 report by Synopsys, which analyzed over 1,700 applications, most of them (96%) contained open source. 76% of total application codebase was open source code.
There are no downsides to open source from the looks of it. You just take an appropriately licensed code, port it to your platform of choice, customize it to fit the task at hand, test it – and it’s done. However, open source software comes with its own risks. It may contain accidental/intentional vulnerabilities or malicious code.
The problem of trust in open source is especially critical for products with heightened security requirements. It takes extra code validation and analysis effort to address that problem. We at Kaspersky have started a service to track open source backdoors and vulnerabilities called Kaspersky Open Source Software Threats Data Feed. As of the end of 2022, it contained data on 3,000 vulnerable and malicious packets stored in popular repositories. Around 35% of exposed vulnerabilities are of high danger level, and another 10% are of critical danger level.
Third-party software in solutions based on KasperskyOS
The Cyber Immunity approach seems to be cut out to solve the problem of using code of unknown quality. And KasperskyOS is the ideal platform to implement this approach. This microkernel operating system enables the creation of inherently Cyber Immune solutions from a variety of small building blocks. This is possible thanks to the principles of isolation and control of interactions implemented in KasperskyOS. Of course, you have to follow a special methodology to develop a Cyber Immune solution: articulate security objectives and assumptions, use a proper approach to architecture design, employ the right SDL practices and various testing methods.
For details on the Cyber Immunization process, refer to the article “How we built a Cyber Immune product using an open source library: stages, pitfalls, solutions”. In that article, Sergey Yakovlev, the head of the KasperskyOS-based thin client development team, discusses at length how various open source components were used to create a real commercial product featuring Cyber Immunity, and how these had to me modified.

Third-party software in solutions based on KasperskyOS
The Cyber Immunity approach seems to be cut out to solve the problem of using code of unknown quality. And KasperskyOS is the ideal platform to implement this approach. This microkernel operating system enables the creation of inherently Cyber Immune solutions from a variety of small building blocks. This is possible thanks to the principles of isolation and control of interactions implemented in KasperskyOS. Of course, you have to follow a special methodology to develop a Cyber Immune solution: articulate security objectives and assumptions, use a proper approach to architecture design, employ the right SDL practices and various testing methods.
For details on the Cyber Immunization process, refer to the article “How we built a Cyber Immune product using an open source library: stages, pitfalls, solutions“. In that article, Sergey Yakovlev, the head of the KasperskyOS-based thin client development team, discusses at length how various open source components were used to create a real commercial product featuring Cyber Immunity, and how these had to me modified.
The cost of porting open source to KasperskyOS
This is fairly simple thanks to the almost full POSIX compatibility of KasperskyOS. The article will take you through the process of porting a FreeRDP library to a thin client’s operating system. This is an open source implementation of an RDP client – a component for connection to remote desktops via Remote Desktop protocol by Microsoft. Despite the library’s fair size – about 400,000 lines of code – not so many modifications were required. Some functions had to be added; unsupported ones were removed, such as fork(). Almost all functions were tested, some defects were spotted and corrected. It took about 30 commits, which you must agree, isn’t that much.
For all those interested in the details of Cyber Immune development, we recommend the article “How we built a Cyber Immune product using an open source library: stages, pitfalls, solutions“.