An operating system’s kernel is the key architectural component responsible for communication between user applications and hardware. KasperskyOS is based on a microkernel developed by Kaspersky. The microkernel is written from scratch and doesn’t use Linux kernel code.
The term “microkernel” implies that only the most critical system operation mechanisms are located in the kernel, while less important functions are ordinary applications. This makes it much easier to ensure that the kernel code is free of errors and vulnerabilities, and that the attack surface is minimal.
Microkernel architecture is the gold standard in developing secure operating systems that don’t require additional security tools. As long as the methodology is followed, such an operating system is secure by design.
 Full screen
Full screen
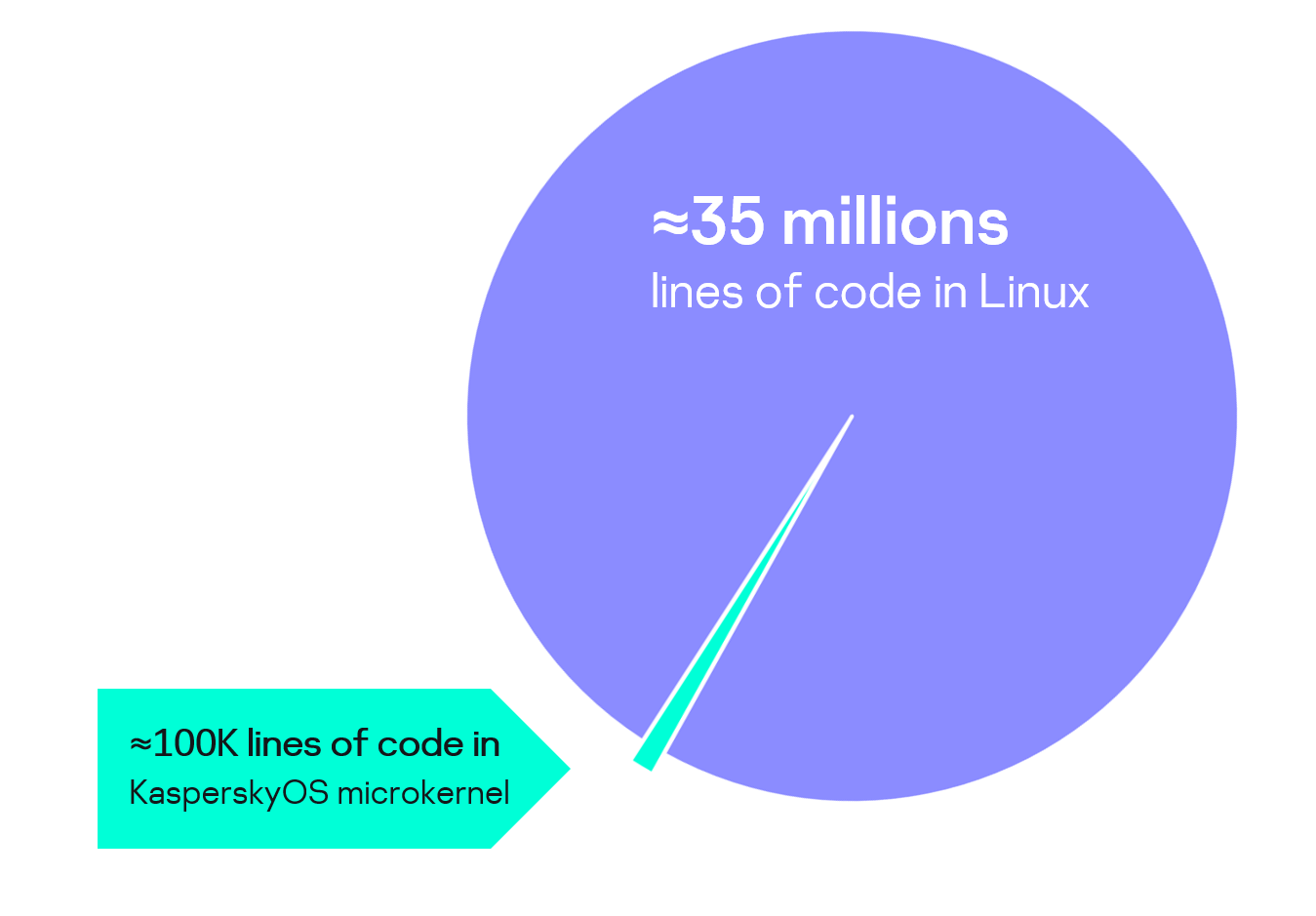
Size of the KasperskyOS microkernel code compared to the monolithic kernel of a general-purpose system
KasperskyOS microkernel is a proprietary Kaspersky development. The design and implementation of all microkernel parts serve to accomplish the main goal: create a secure operating system.
The KasperskyOS kernel contains only a few dozen thousand lines of code. The smaller the kernel size, the fewer potential vulnerabilities it has and the easier it is to formally verify. To compare: monolithic kernels can include tens of millions of code lines.
There are only three system calls and only one IPC interface in KasperskyOS. This keeps the attack surface to a minimum.
The KasperskyOS microkernel is designed to take full advantage of Kaspersky Security System capabilities.
A number of libraries have been developed for KasperskyOS that provide partial POSIX compatibility, thus simplifying the creation and porting of applications.
The KasperskyOS kernel is responsible for functions that can only be performed in privileged mode:
All other operating system functions, including drivers, file systems, and network stacks, are moved to user mode.
The KasperskyOS kernel guarantees complete isolation of IT system components. The only IPC type provided by the kernel is synchronous messaging (request–response). Each message is sent to the Kaspersky Security System to check for compliance with the specified security policy. The kernel only delivers the message if the policy allows it.