Isolation is the cornerstone of a secure information system. However, there must be interaction between system components for it to actually work. To tailor solutions to specific tasks, be it the operation of an IoT gateway or a nuclear reactor, it’s necessary to be able to describe various security policies.
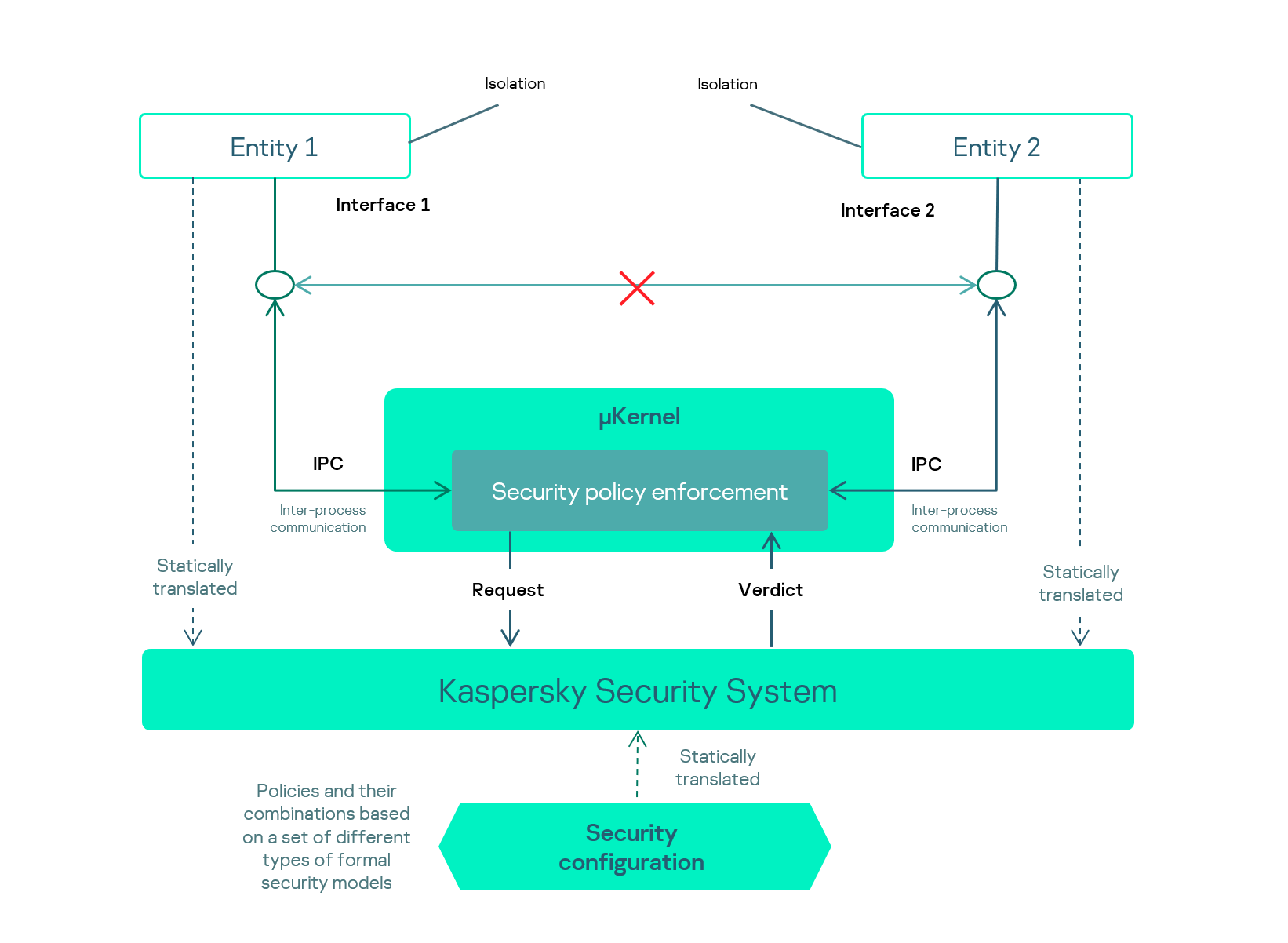
KasperskyOS is designed to handle these and other security tasks using the Kaspersky Security System. All inter-process communications (IPC) pass through this module. It checks each interaction for compliance with security policies, and if it doesn’t comply, it’s blocked.
Even if a component is compromised, Kaspersky Security System eliminates or minimizes any possible damage. Thus the system becomes cyber-immune.
Kaspersky Security System architecture is based on two classic information security concepts: MILS (Multiple Independent Levels of Security) architecture and FLASK (Flux Advanced Security Kernel).
 Full screen
Full screen
KasperskyOS components interaction scheme
Any interaction that isn't explicitly allowed by the security policy is blocked. The Default Deny principle underlies all secure solutions based on KasperskyOS.
The solution developers can combine many different models to create policies that best meet your security goals. The PSL language is designed to describe the security policy in terms of the solution itself.
The developer doesn't have to write code that implements the security policy. Instead, it's generated by a special compiler based on the PSL description. You can trust code generated on the basis of well-studied models.
The implementation of security policies is separated from the application code. As a result, they can be modified independently, thus significantly simplifying the work of app developers and solution architects.
Kaspersky Security System is a monitor where the kernel sends all IPC messages to check them for compliance with the specified security policy. Moreover, the objects can access Kaspersky Security System directly using a special interface, which opens up additional opportunities for security architects.
To simplify policy creation, we developed a dedicated Policy Specification Language (PSL). The PSL syntax allows you to combine various security models in a single policy, including finite-state and timed automatons, TE (Type Enforcement), role-based access control (RBAC) models, and many others. You can also develop your own policy classes. At the same time, PSL is an expressive language where descriptions are developed in terms of the task.
The Policy Specification Language relieves developers of the need to write security policy implementation or configure the Kaspersky Security System manually. All you need to do is run a special compiler to optimize the Kaspersky Security System code for the selected task from the PSL description.