
In the November issue of the German automation industry magazine SPS-Magazin, an article was published about the NOA concept and how the Cyber Immune approach fits within its tenets. Author: Thomas Menze, Senior Consultant, ARC Advisory Group Europe.
NOA is a concept that aims to make production and plant data easily and securely usable for plant and equipment monitoring and optimization. NOA is based on the idea of opening the automation pyramid and unlocking more data from smart sensors, field devices, mobile devices, and other IT equipment. NOA does not affect the traditional automation structures or the automation system, but rather transmits the data over a second communication channel. NOA is suitable for both existing systems (brownfield) and new installations (greenfield).
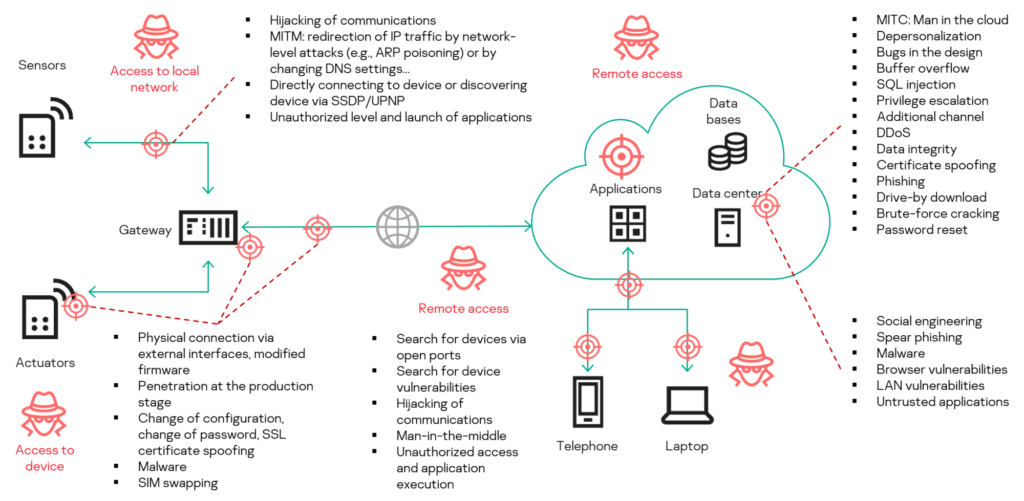
One of the main challenges of NOA is to ensure that the data flow from the core process control domain to the monitoring and optimization domain does not compromise the security goals of core process automation. This is the task of the NOA Security Gateway, which is a component that acts as an interface between the two domains. The NOA Security Gateway has three modules: a data retrieval module, a data provision module, and a verification module. The data retrieval module collects data from the core process control domain and forwards it to the data provision module. The data provision module filters, aggregates and transforms the data according to the requests from the monitoring and optimization domain. The verification module checks the requests for validity, authenticity, and authorization.
The NOA Security concept defines three NOA Security Zones: ‘Core Process Control’, ‘Monitoring & Optimization on-premises’ and ‘Monitoring & Optimization off premises’. These zones have different security levels and protection profiles, which are based on the IEC 62443-3-3 standard. The protection profiles are called NOA Basic and NOA Extended, and they include security requirements that apply to both the automation system in general and the NOA Security Gateway in particular.
The motivation for developing NOA and its security concept is to enable a wide range of digital use cases that demonstrate the great potential of the new concept. By using NOA, plant operators can benefit from improved efficiency, reliability, safety and sustainability of their production processes.
Let’s first look at the operating systems currently used for OT automation. These were developed in the 1970s. The systems consist of different functional layers. First is the base layer, or firmware, which controls hardware-related functions. This is followed by the application layer, for the operating software. Above this is the security layer, which prevents unauthorized access. However, if this security layer is overcome, the attacker has access to the subordinate layers and can manipulate functions there. This is why the Cyber Immunity concept is structured differently. The architecture is based on a so-called microkernel structure.
One characteristic of microkernels is their short code length. In terms of software, this means that their functions and architecture are simple and logically structured.
Microkernels provide a minimum of basic process management functions and hardware functions. Most of the hardware and software function is run outside the microkernel. This can significantly reduce the attack surface.
In addition to traditional microkernel functions, Kaspersky also implements inter-process communication (IPC) to provide strong isolation between security domains. In the context of dividing the operating system environment into security domains (processes). Data flow between processes is monitored by a special framework called Kaspersky Security System.
The microkernel manages the applications and provides strong, controlled IPC. This means that drivers, system services, applications, etc. are moved into the user space and isolated from each other. This isolation is controlled and monitored by security policies. If one of the system components attempts to store data and/or send data to another location, it can only do so if specified in a security policy defined for the solution. This approach supports the NOA concept, because data flow is only possible in a preconfigured direction.
The core function of Cyber Immunity means that an IIoT device can be networked with other automation devices in a non-reactive manner without additional security functions.
This is an analogy to the NAMUR NOA concept discussed earlier. With NOA, networking is limited to monitoring and optimization. If more and more IIoT components are used in industry in the future, then the Cyber Immunity concept will simplify the patching of these IIoT components.
Often IIoT components are developed without a focus on IT security. Authentication is often built into these components, but that’s about it. The use of “vulnerable software” in cyber-physical systems means that cyber threats are increasingly compromising the security of people in the physical world.
This is exactly what Cyber Immunity was designed for, as this concept hardens networked OT systems to achieve defined levels of security. A cyber-physical system can be called immune if cyber-attacks prove ineffective and do not affect the function of the system. The concept of Cyber Immunity means that the risk of entire classes of cyber-attacks is eliminated. This is a critical advantage for critical infrastructure. Industry plans to increase the effectiveness of its machinery and equipment. This can be done, for example, with the help of IIoT sensors that monitor and optimize processes. On the other hand, the deployment of IIoT sensors is delayed by uncertainties due to possible cyber-attacks. Here, Cyber Immunity in the gateways helps to operate a secure IIoT infrastructure.

In the November issue of the German automation industry magazine SPS-Magazin, an article was published about the NOA concept and how the Cyber Immune approach fits within its tenets. Author: Thomas Menze, Senior Consultant, ARC Advisory Group Europe.
NOA is a concept that aims to make production and plant data easily and securely usable for plant and equipment monitoring and optimization. NOA is based on the idea of opening the automation pyramid and unlocking more data from smart sensors, field devices, mobile devices, and other IT equipment. NOA does not affect the traditional automation structures or the automation system, but rather transmits the data over a second communication channel. NOA is suitable for both existing systems (brownfield) and new installations (greenfield).
One of the main challenges of NOA is to ensure that the data flow from the core process control domain to the monitoring and optimization domain does not compromise the security goals of core process automation. This is the task of the NOA Security Gateway, which is a component that acts as an interface between the two domains. The NOA Security Gateway has three modules: a data retrieval module, a data provision module, and a verification module. The data retrieval module collects data from the core process control domain and forwards it to the data provision module. The data provision module filters, aggregates and transforms the data according to the requests from the monitoring and optimization domain. The verification module checks the requests for validity, authenticity, and authorization.
The NOA Security concept defines three NOA Security Zones: ‘Core Process Control’, ‘Monitoring & Optimization on-premises’ and ‘Monitoring & Optimization off premises’. These zones have different security levels and protection profiles, which are based on the IEC 62443-3-3 standard. The protection profiles are called NOA Basic and NOA Extended, and they include security requirements that apply to both the automation system in general and the NOA Security Gateway in particular.
The motivation for developing NOA and its security concept is to enable a wide range of digital use cases that demonstrate the great potential of the new concept. By using NOA, plant operators can benefit from improved efficiency, reliability, safety and sustainability of their production processes.

Let’s first look at the operating systems currently used for OT automation. These were developed in the 1970s. The systems consist of different functional layers. First is the base layer, or firmware, which controls hardware-related functions. This is followed by the application layer, for the operating software. Above this is the security layer, which prevents unauthorized access. However, if this security layer is overcome, the attacker has access to the subordinate layers and can manipulate functions there. This is why the Cyber Immunity concept is structured differently. The architecture is based on a so-called microkernel structure.
One characteristic of microkernels is their short code length. In terms of software, this means that their functions and architecture are simple and logically structured.
Microkernels provide a minimum of basic process management functions and hardware functions. Most of the hardware and software function is run outside the microkernel. This can significantly reduce the attack surface.
In addition to traditional microkernel functions, Kaspersky also implements inter-process communication (IPC) to provide strong isolation between security domains. In the context of dividing the operating system environment into security domains (processes). Data flow between processes is monitored by a special framework called Kaspersky Security System.
The microkernel manages the applications and provides strong, controlled IPC. This means that drivers, system services, applications, etc. are moved into the user space and isolated from each other. This isolation is controlled and monitored by security policies. If one of the system components attempts to store data and/or send data to another location, it can only do so if specified in a security policy defined for the solution. This approach supports the NOA concept, because data flow is only possible in a preconfigured direction.
The core function of Cyber Immunity means that an IIoT device can be networked with other automation devices in a non-reactive manner without additional security functions.
This is an analogy to the NAMUR NOA concept discussed earlier. With NOA, networking is limited to monitoring and optimization. If more and more IIoT components are used in industry in the future, then the Cyber Immunity concept will simplify the patching of these IIoT components.
Often IIoT components are developed without a focus on IT security. Authentication is often built into these components, but that’s about it. The use of “vulnerable software” in cyber-physical systems means that cyber threats are increasingly compromising the security of people in the physical world.
This is exactly what Cyber Immunity was designed for, as this concept hardens networked OT systems to achieve defined levels of security. A cyber-physical system can be called immune if cyber-attacks prove ineffective and do not affect the function of the system. The concept of Cyber Immunity means that the risk of entire classes of cyber-attacks is eliminated. This is a critical advantage for critical infrastructure. Industry plans to increase the effectiveness of its machinery and equipment. This can be done, for example, with the help of IIoT sensors that monitor and optimize processes. On the other hand, the deployment of IIoT sensors is delayed by uncertainties due to possible cyber-attacks. Here, Cyber Immunity in the gateways helps to operate a secure IIoT infrastructure.