
In mid-March, the Industrial Internet Consortium published an important document for industrial IT systems and the internet of things — a description of the Multiple Independent Levels of Security (MILS) architectural approach. Its principles are widely used in building reliable, secure systems in transport, industry and corporate environments. The document was authored by Ekaterina Rudina, a Kaspersky ICS Cyber Emergency Response Team analyst, and Rance J. Delong, a security consultant for The Open Group.

The document describes how MILS ensures information and functional security, reliability and resilience of systems, as well as the personal safety of users. It details the basic concepts of the approach, including isolation, separation and control of information flows. It also covers the role of division into domains and organization of cross-domain interaction in the implementation of security policy architecture. The document is available to specialists with various technical and business interests, and will be useful for both developers and managers focusing on creating safe and reliable systems.
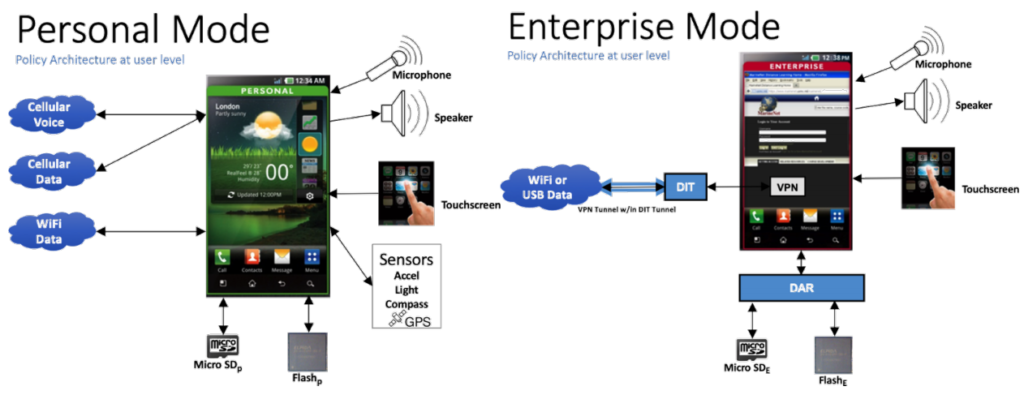
It also provides real-world MILS application examples, including the construction of management systems for railway infrastructure and smart power supply networks, and communications in an air traffic control system. The Trusted Smart Phone platform section clearly shows how information security is ensured in a corporate environment. It provides safe mobile device operation for both corporate and personal purposes.
KasperskyOS is another example of MILS in action. From the very beginning, the system was developed on the basis of this approach, implementing the core of separation and isolation of domains (drivers, applications, libraries). The Kaspersky Security System module controls cross-domain communications and enables configurations meeting the requirements of the adaptive MILS platform.
Entitled MILS Architectural Approach Supporting Trustworthiness of IIoT Solutions, the document is an important step towards forming international standards for the design of secure industrial systems.
The Industrial Internet Consortium is a non-profit organization founded in 2014 by AT&T, Cisco, General Electric, IBM and Intel. Today, more than 250 Consortium members are accelerating the growth of the industrial internet market by identifying, testing and promoting best practices.
The Open Group is an industry consortium formed to establish neutral open technology standards for computing infrastructure and serves as a certification body for UNIX.

In mid-March, the Industrial Internet Consortium published an important document for industrial IT systems and the internet of things — a description of the Multiple Independent Levels of Security (MILS) architectural approach. Its principles are widely used in building reliable, secure systems in transport, industry and corporate environments. The document was authored by Ekaterina Rudina, a Kaspersky ICS Cyber Emergency Response Team analyst, and Rance J. Delong, a security consultant for The Open Group.

The document describes how MILS ensures information and functional security, reliability and resilience of systems, as well as the personal safety of users. It details the basic concepts of the approach, including isolation, separation and control of information flows. It also covers the role of division into domains and organization of cross-domain interaction in the implementation of security policy architecture. The document is available to specialists with various technical and business interests, and will be useful for both developers and managers focusing on creating safe and reliable systems.
It also provides real-world MILS application examples, including the construction of management systems for railway infrastructure and smart power supply networks, and communications in an air traffic control system. The Trusted Smart Phone platform section clearly shows how information security is ensured in a corporate environment. It provides safe mobile device operation for both corporate and personal purposes.

KasperskyOS is another example of MILS in action. From the very beginning, the system was developed on the basis of this approach, implementing the core of separation and isolation of domains (drivers, applications, libraries). The Kaspersky Security System module controls cross-domain communications and enables configurations meeting the requirements of the adaptive MILS platform.
Entitled MILS Architectural Approach Supporting Trustworthiness of IIoT Solutions, the document is an important step towards forming international standards for the design of secure industrial systems.
The Industrial Internet Consortium is a non-profit organization founded in 2014 by AT&T, Cisco, General Electric, IBM and Intel. Today, more than 250 Consortium members are accelerating the growth of the industrial internet market by identifying, testing and promoting best practices.
The Open Group is an industry consortium formed to establish neutral open technology standards for computing infrastructure and serves as a certification body for UNIX.