
In physics there is an analogy method. This is when phenomena from one domain are mentally replaced by phenomena from another domain because both are described by the same differential equations. Complex mechanical systems can in some cases be replaced by analogous electrical circuits, for example, by comparing the force of friction with the corresponding value of resistance, velocity with the value of current, and so on.
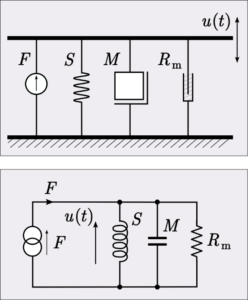
Why is this done? Because the same problem in another ‘world’ may be easier to solve than the original problem.
The same equations have the same solutions.
Another curious example is string theory. Physicists did not know how to describe the behavior of elementary particles, and in the late 1960s Gabriele Veneziano and Mahiko Suzuki suggested that the formula could be analogous to the formula describing the behavior of a string, derived by Euler in the 18th century. And they were right!
The analogy method has also been applied in the world of digitalization and cybersecurity.
It turned out that many of the challenges facing developers of modern software and hardware systems are almost analogous to the problems in the field of corporate IT. Therefore, it became possible to take mature approaches from the world of “corporate IT” that have been developed over decades and transfer them to another world – the world of creating secure cybersystems. For example, in the world of cybersystems development there is the concept of MILS (Multiple Independent Levels of Security), which represents a successful outcome of this migration. In essence, MILS divides the cybersystem into multiple isolated domains, and the interactions between these domains are carefully controlled. These principles are virtually identical to the approaches used in enterprise IT.
| ‘World’ of cybersystems (MILS attributes) | ‘World’ of corporate IT |
| Division into security domains | Network segmentation |
| Decision points | Firewalls |
| Local policies within a domain | Access control lists (ACL) |
MILS is a mature, well-developed concept that has been successfully applied in global practice. In fact, the KasperskyOS operating system used it as one of its main architectural principles more than 10 years ago.

In physics there is an analogy method. This is when phenomena from one domain are mentally replaced by phenomena from another domain because both are described by the same differential equations. Complex mechanical systems can in some cases be replaced by analogous electrical circuits, for example, by comparing the force of friction with the corresponding value of resistance, velocity with the value of current, and so on.

Why is this done? Because the same problem in another ‘world’ may be easier to solve than the original problem.
The same equations have the same solutions.
Another curious example is string theory. Physicists did not know how to describe the behavior of elementary particles, and in the late 1960s Gabriele Veneziano and Mahiko Suzuki suggested that the formula could be analogous to the formula describing the behavior of a string, derived by Euler in the 18th century. And they were right!
The analogy method has also been applied in the world of digitalization and cybersecurity.
It turned out that many of the challenges facing developers of modern software and hardware systems are almost analogous to the problems in the field of corporate IT. Therefore, it became possible to take mature approaches from the world of “corporate IT” that have been developed over decades and transfer them to another world – the world of creating secure cybersystems. For example, in the world of cybersystems development there is the concept of MILS (Multiple Independent Levels of Security), which represents a successful outcome of this migration. In essence, MILS divides the cybersystem into multiple isolated domains, and the interactions between these domains are carefully controlled. These principles are virtually identical to the approaches used in enterprise IT.
| ‘World’ of cybersystems (MILS attributes) | ‘World’ of corporate IT |
| Division into security domains | Network segmentation |
| Decision points | Firewalls |
| Local policies within a domain | Access control lists (ACL) |
MILS is a mature, well-developed concept that has been successfully applied in global practice. In fact, the KasperskyOS operating system used it as one of its main architectural principles more than 10 years ago.