
In today’s highly connected world, the number of ways an attack can be developed against a system by compromising just a single component is enormous. As a consequence, creating a secure system is understandably challenging: all its components need to be carefully protected and verified. But given the high percentage of third-party code in most information systems, and their multi-component nature, “protecting everything” in practice is an impossible task.
There is, however, a solution: you need to divide all system components into three groups — according to the security objectives you have set.
An important part of a coach’s job in team sports is to position the players effectively in relation to each other. The same applies here: it’s important to place the three categories of components wisely. The untrusted ones are placed on the edge of the system, the trusted ones in the center, and the highly trusted ones in between.
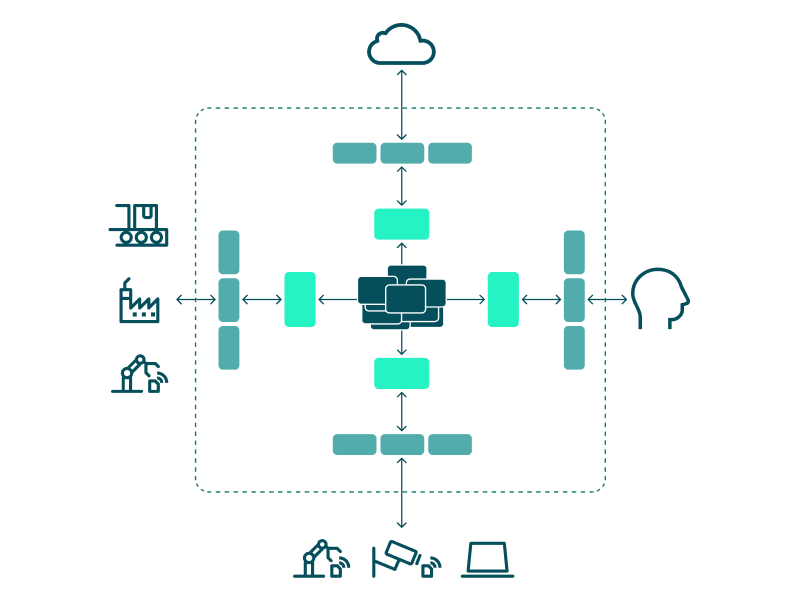
In this arrangement basic protection and verification are sufficient for untrusted components, since the security objectives do not depend on them. The protection and verification requirements for trusted components are by definition high, but they can be mitigated because these components are “covered” by the highly trusted ones and find themselves somewhat in the rear. It’s only the highly trusted components themselves, of which there are usually few, that need to be protected and checked with the utmost care.
So we end up with a heterogeneous system in which only a small proportion of the components need to be carefully protected and checked. As with the Pareto principle, 20% of the effort gets you 80% of the result. In practice, the ratio can be even higher.
This is the three markers method used in the development of Cyber Immune solutions. It helps you create a system that can be trusted from components most of which cannot be trusted. Read more about the Cyber Immune approach to development here and in subsequent posts.

In today’s highly connected world, the number of ways an attack can be developed against a system by compromising just a single component is enormous. As a consequence, creating a secure system is understandably challenging: all its components need to be carefully protected and verified. But given the high percentage of third-party code in most information systems, and their multi-component nature, “protecting everything” in practice is an impossible task.
There is, however, a solution: you need to divide all system components into three groups — according to the security objectives you have set.
An important part of a coach’s job in team sports is to position the players effectively in relation to each other. The same applies here: it’s important to place the three categories of components wisely. The untrusted ones are placed on the edge of the system, the trusted ones in the center, and the highly trusted ones in between.

In this arrangement basic protection and verification are sufficient for untrusted components, since the security objectives do not depend on them. The protection and verification requirements for trusted components are by definition high, but they can be mitigated because these components are “covered” by the highly trusted ones and find themselves somewhat in the rear. It’s only the highly trusted components themselves, of which there are usually few, that need to be protected and checked with the utmost care.
So we end up with a heterogeneous system in which only a small proportion of the components need to be carefully protected and checked. As with the Pareto principle, 20% of the effort gets you 80% of the result. In practice, the ratio can be even higher.
This is the three markers method used in the development of Cyber Immune solutions. It helps you create a system that can be trusted from components most of which cannot be trusted. Read more about the Cyber Immune approach to development here and in subsequent posts.